For efficient and secure management of your system access
The implementation of multi-factor authentication and “zero trust” requires the use of security keys. Security keys supporting multiple protocols allow the implementation of “passwordless” authentications that are more secure and efficient than simple authentication.
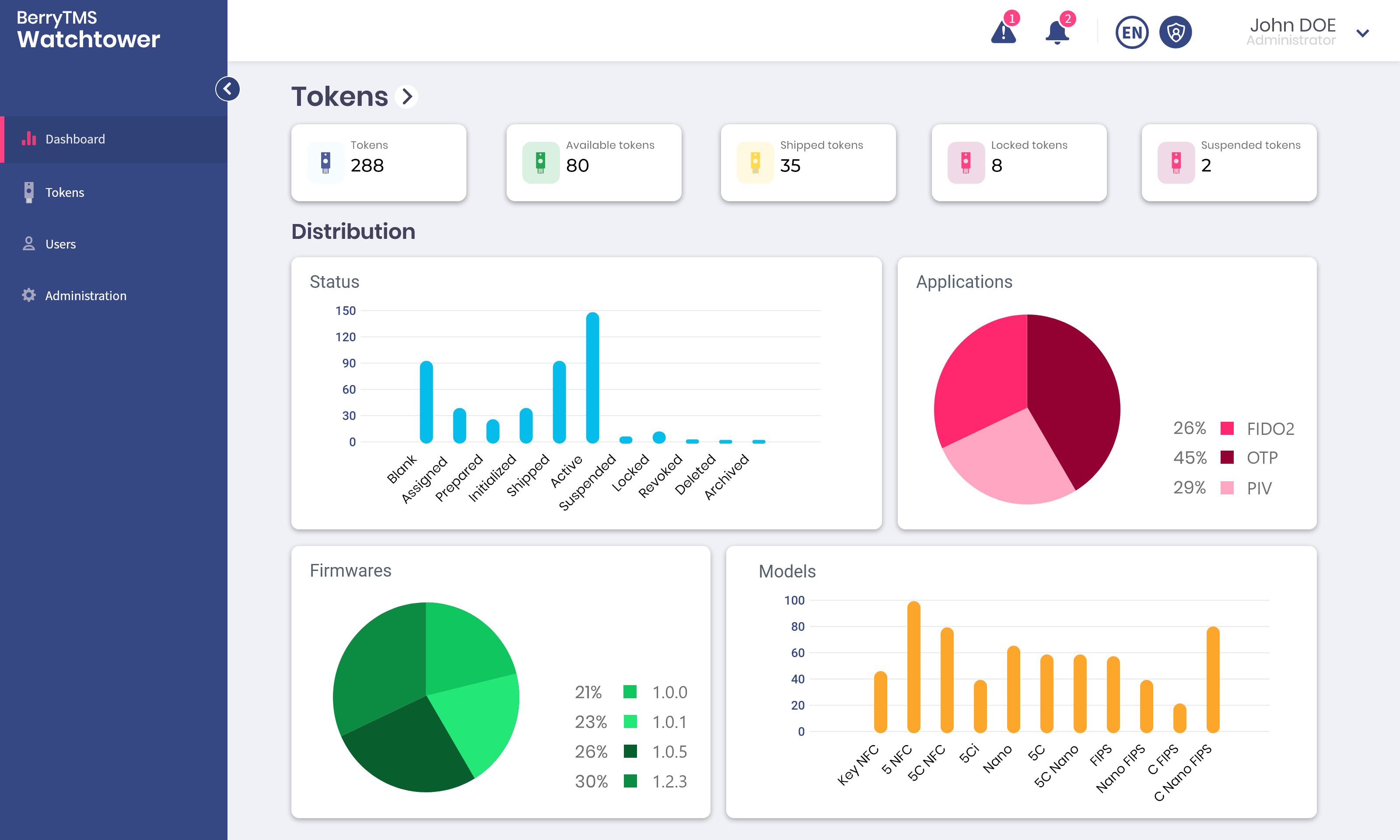
However, setting up authentication solutions based on physical tokens raises the question of managing their life cycle: from initialization to deployment, including fleet supervision.
BerryTMS allows you to:
- Deploy security keys easily, securely and in large numbers
- Manage the life cycle of the various credentials contained in the keys
- Get a complete view of the use of keys in the company
Find out how to optimize your key management
Multiple use cases
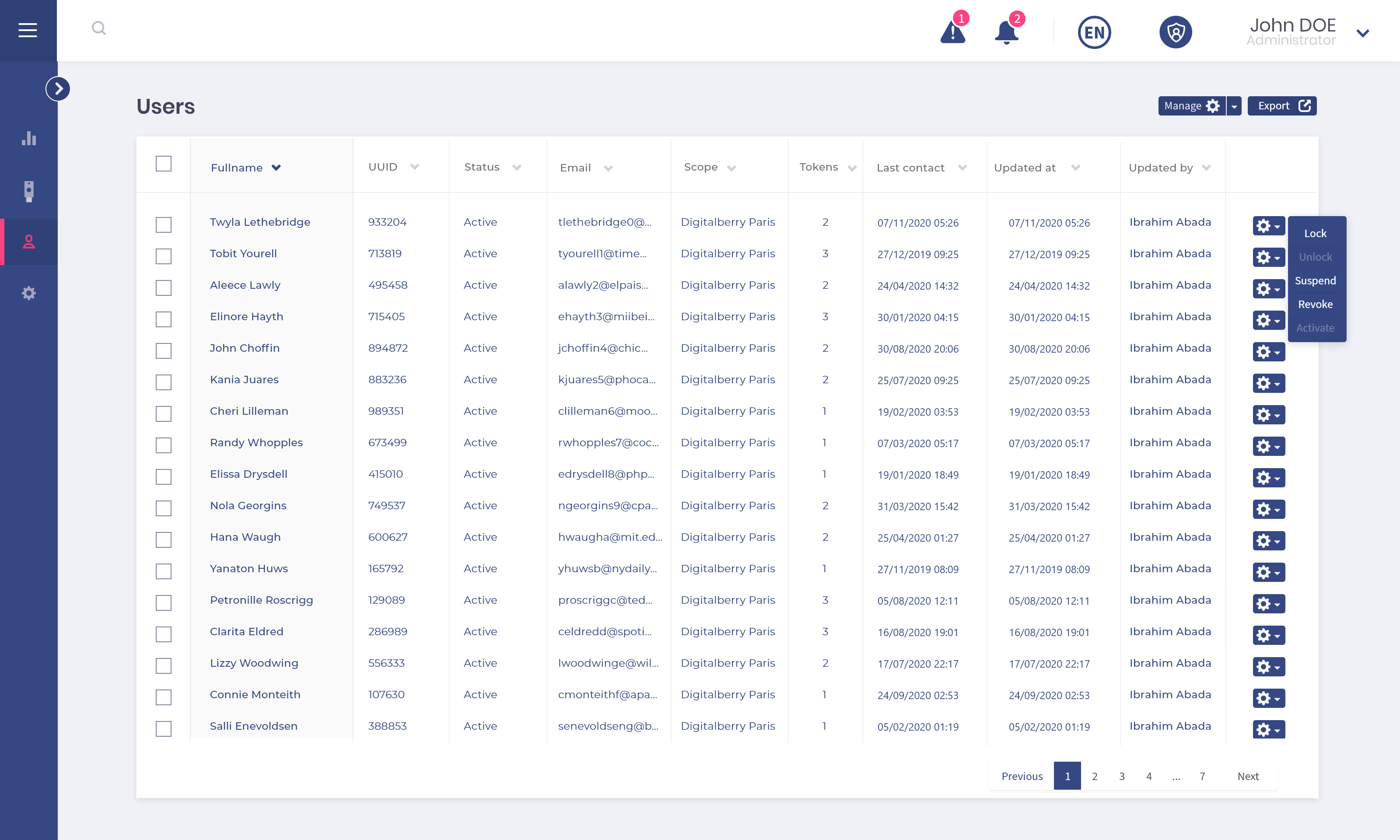
Enroll your users appropriately
Manage your keys remotely and securely in order to enroll your users. Define the type of enrollment by choosing among those proposed in the solution: enrollment at a distance, face to face or for VIPs. Customize the secrets generated in the key during enrollment based on the user.
Manage the lifecycle of your security keys
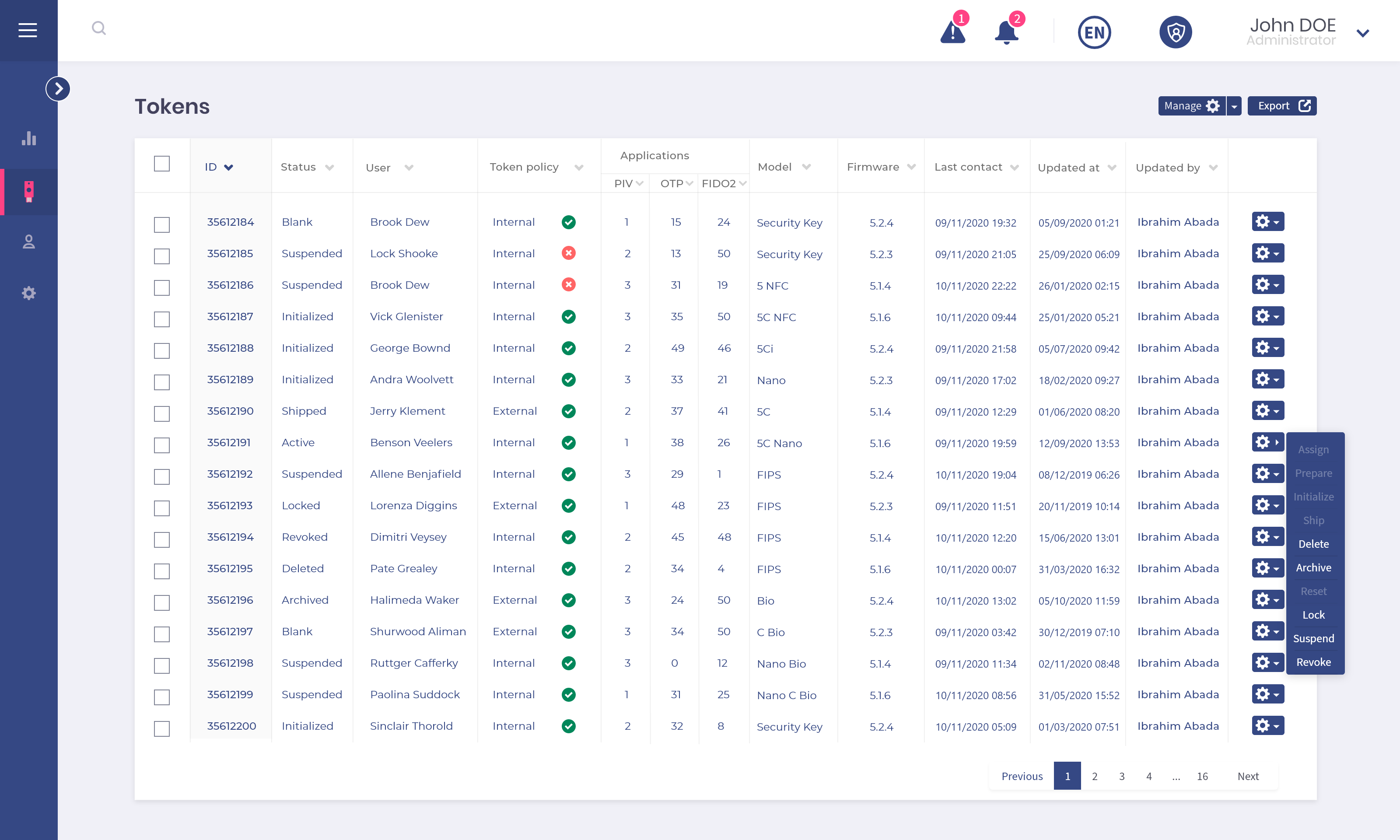
Apply your management policies to all of your keys continuously and monitor the lifecycle of your entire fleet in real time.
Unlock the keys or revoke access to your IS by blocking compromised keys.
Replace your security keys in the event of loss or forgetting to ensure continuity of access.
BerryTMS in brief
Management of USB security keys, smart cards and HSMs
Global monitoring and reporting of keys and secrets
Audit trails for traceability and non-repudiation
Guided processes for key management
Definition and customization of policies, rights and access
Integrated Vault of Secrets with HSM
Digitalberry supports you in the framing, management and production of its centralized key management solution, adapted to your environment.