

There are three main types of TLS (formerly SSL) certificate for protecting a website: domain validation (DV), organization validation (OV) and extended validation (EV). There is often much confusion about the different TLS certificates, not to mention users who struggle to understand what the padlock and “not secure” in their browser’s address bar really mean. Let’s take a closer look at the different certificates and the levels of security they offer.
Pressure from web giants, and Google in particular, to increase website security is pushing administrators to make the switch to HTTPS, where the secure connection is encrypted by a session key protected by a TLS certificate. When a website isn’t protected by a TLS certificate, browsers now warn that it is “not secure”, which does nothing to build trust between the user and the company whose website they are visiting. There are three types of TLS certificate, all issued by a Certificate Authority (CA) which is solely authorized to issue certificates.
Domain validation (DV) certificate
This certificate provides the lowest level of security and is the cheapest and easiest to obtain. It simply exchanges a few e-mails to ensure that the certificate owner is the domain owner. The Certificate Authority doesn’t verify the organization’s identity. This type of certificate is used to secure blogs, wikis or websites which do not involve transferring sensitive data or monetary transactions. DV certificates can be issued to websites that are not completely reliable or that contain malware or other fraudulent programs as the domain owner isn’t verified. For example, Let’s encrypt, a certificate authority operated by the non-profit Internet Security Research Group (ISRG), issues domain validation certificates free of charge.
Organization validation (OV) certificate
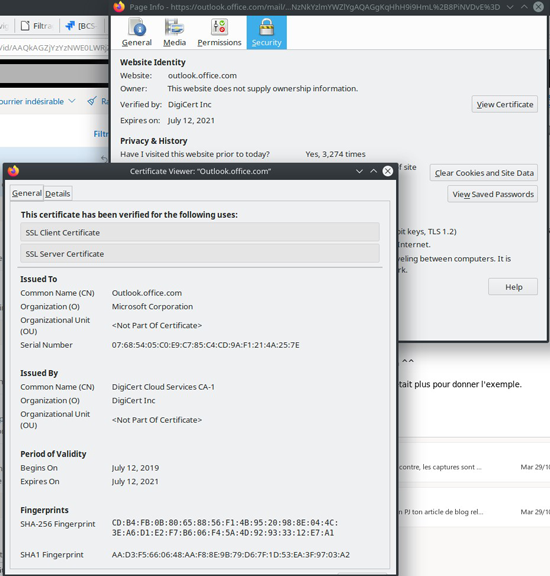
This type of certificate offers a higher level of security. The Certificate Authority first checks that the requester is the owner of the organization the certificate is requested for. But it doesn’t verify their identity. Verification takes longer than for a DV certificate. After a few communications via e-mail, postal mail or telephone, certificates can be delivered within a few days. For example, the certificate used by Outlook webmail certifies that the Microsoft Corporation organization legally exists but doesn’t verify its identity.
Extended validation (EV) certificate
Extended validation certificates offer the highest level of security. The checks on the requester are more extensive, such as legal existence of the company, veracity of all the information provided as evidence and verification of the organization manager’s identity.
This type of certificate is mainly used by sites allowing bank transactions (banking, government, etc.). When such certificates are used, browsers display the company name in green in the address bar, reinforcing the user’s sense of security.
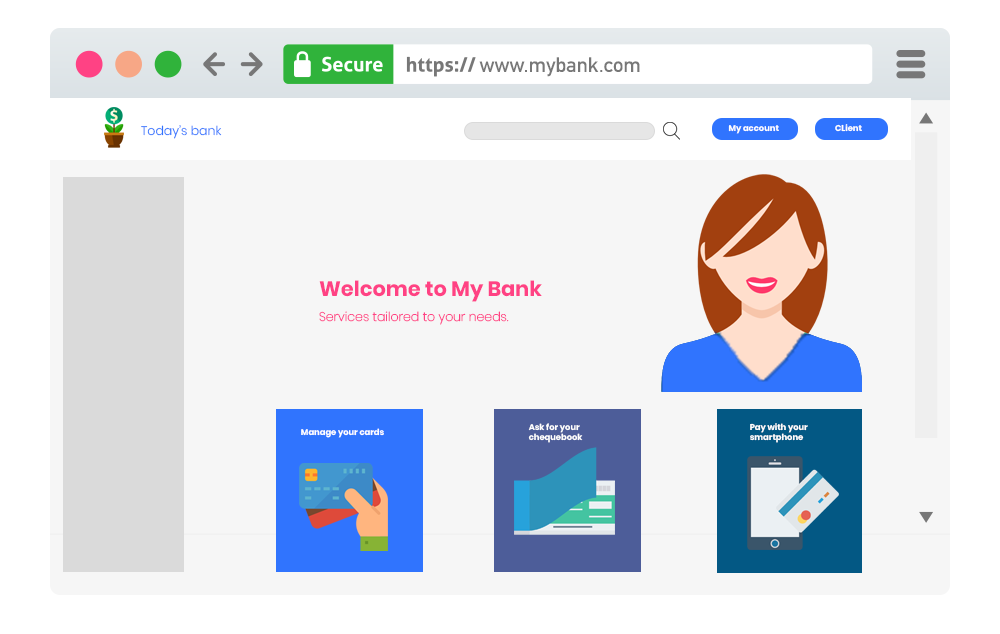
Although it’s clear that extended validation certificates afford the best protection and trust for users, the solution comes at a significant annual cost. Only an in-depth analysis of the criticality of the data transiting between the server and the users can determine which certificate should be implemented.
